Learn how to manage Low-Code/No-Code (LCNC) governance
Mastering Low-Code/No-Code (LCNC) Governance: A Guide for the Modern Enterprise
The rapid rise of Low-Code/No-Code (LCNC) platforms has fundamentally shifted the software development landscape. No longer restricted to professional IT teams, application development has been "democratized," allowing citizen developers—business users with little to no formal coding background—to build tools that solve immediate operational needs.
While this speed and agility are transformative, they bring significant challenges. Without a robust strategy for application governance, organizations face a surge in unmanaged software, leading to a massive shadow IT risk. For an enterprise-scale LCNC adoption to be successful, IT leaders must implement a framework that balances innovation with security, compliance, and quality.
Understanding the Governance Gap
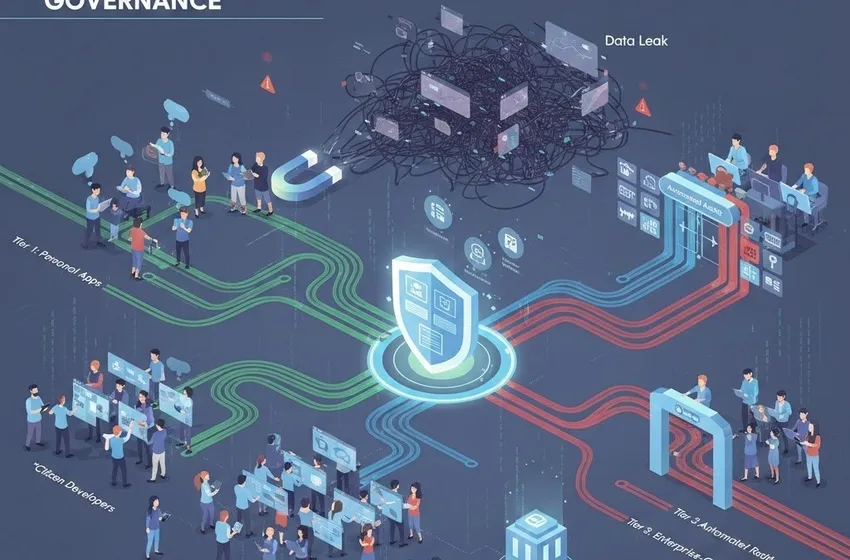
LCNC platforms are designed for speed. They use visual interfaces, drag-and-drop components, and pre-built connectors to bypass the traditional development lifecycle. However, when thousands of employees have the power to create apps, the "app gap" often turns into an "app sprawl."
Managing the proliferation of applications requires more than just picking a platform; it requires a shift in mindset. IT must move from being a "gatekeeper" (which often triggers shadow IT when processes are too slow) to being an "enabler" that provides the guardrails for safe innovation.
The Three Pillars of LCNC Governance
1. Security and Risk Mitigation
The primary fear for most CISOs regarding LCNC is data leakage. Citizen developers may unintentionally connect an internal database to an unsecure third-party API or fail to implement proper role-based access controls (RBAC).
-
Data Perimeter: Define which data sources are "off-limits" and which can be used for LCNC projects.
-
Identity Management: Ensure all LCNC apps use corporate Single Sign-On (SSO) to maintain visibility into who is accessing what.
2. Compliance and Regulatory Alignment
In regulated industries like finance or healthcare, an app built by a marketing manager is subject to the same GDPR or HIPAA rules as a core banking system. Application governance must include automated checks to ensure apps don't violate data residency or privacy laws.
3. Quality and Technical Debt
"Quick and dirty" apps often become critical "legacy" tools overnight. If a citizen developer leaves the company, who maintains their apps? Without quality standards, the organization accumulates technical debt that eventually slows down the entire IT department.
Strategies for Enterprise-Scale LCNC Adoption
To scale successfully, organizations often adopt a Center of Excellence (CoE) model. This central body establishes the rules of engagement while allowing departments to move fast.
The Tiered Application Model
Not all apps are created equal. Effective governance uses a tiered approach:
-
Tier 1 (Personal/Productivity): Low risk, used by one person. Light oversight.
-
Tier 2 (Departmental): Used by a team. Requires basic security review and documentation.
-
Tier 3 (Enterprise-Critical): High risk, touches sensitive data. Requires IT partnership, rigorous testing, and formal handoff.
Mitigating Shadow IT Risk
Shadow IT risk flourishes in the dark. When employees feel that IT is a roadblock, they turn to unsanctioned SaaS tools. By providing an official LCNC platform with a clear path to approval, IT brings these users into the light.
-
Visibility: Use platform-native admin centers to monitor every app created in the environment.
-
Education: Train citizen developers not just on how to build, but on the why of security and compliance.