Master Cloud Native security with Policy-as-Code
The core value of PaC is the "shift-left" principle for security. By codifying policies, validation checks can be integrated directly into the CI/CD pipeline, catching security misconfigurations and compliance violations early. This is exponentially more efficient and less costly than finding and fixing issues in a live production environment.
Policy Enforcement Points in Cloud Native Environments
Policies must be enforced at multiple stages to build a robust security posture:
- Design/Code: Policies are used to validate Infrastructure-as-Code (IaC) templates (e.g., Terraform, Kubernetes manifests) before deployment.
- Build/Pipeline: Policies check container images for vulnerabilities and ensure they adhere to baseline configurations.
- Deployment/Runtime: This is where admission controllers—a vital component of Kubernetes security—come into play, providing real-time enforcement.
- Audit/Continuous Monitoring: Policies are continuously evaluated against the live state of the environment to detect configuration drift and flag non-compliant resources.
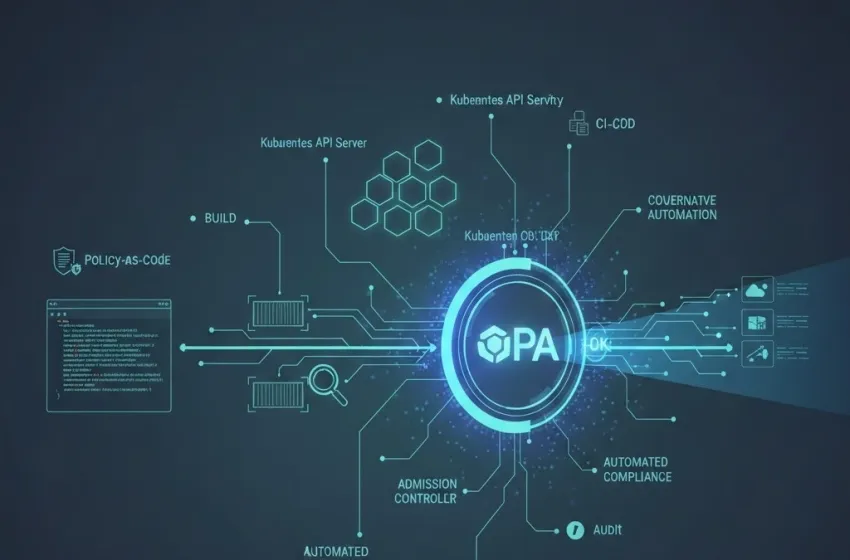
Open Policy Agent (OPA): The Policy Engine Standard
The most prominent and widely adopted tool for implementing policy-as-code in the cloud-native ecosystem is the Open Policy Agent (OPA). OPA is a general-purpose, open-source policy engine that decouples policy decision-making from the application or service. It provides a unified policy layer across the entire stack.
Key Features of OPA
- Rego Language: OPA policies are written using Rego, a high-level, declarative language specifically designed for expressing policies over structured data (like JSON or YAML). Rego allows policies to be simple ("Is this request allowed?") or complex, considering multiple data points—such as the user's role, the time of day, and the resource being accessed—to make a nuanced decision.
- Decoupled Decision Making: OPA receives an input (a JSON object representing a request or a resource manifest), evaluates it against the defined policies, and returns a decision (typically an allow or deny result, or a structured JSON response). This separation means the application or service doesn't need to embed complex policy logic, making it cleaner and easier to maintain.
- Versatility: OPA isn't limited to Kubernetes. It can be used for authorization in microservices, API gateways (like Envoy or Istio), CI/CD pipelines, and even for SSH/Sudo rules, making it the bedrock for consistent governance automation across diverse infrastructure.
Admission Controllers and Kubernetes Security
The most critical use case for policy-as-code in the Cloud Native security domain is within Kubernetes security using admission controllers.
Admission controllers are a feature of the Kubernetes API server that intercept requests before they are persisted to the cluster's data store (etcd). They act as mandatory security and governance checkpoints. There are two main types:
- Validating Admission Controllers: These check if a request complies with a set of policies. If the resource violates a policy (e.g., a Pod is configured to run as a privileged container), the request is rejected, and the resource is never created.
- Mutating Admission Controllers: These can modify a request to inject required configurations (e.g., automatically adding a specific label, setting a default resource limit, or attaching a specific service account) before the validation phase.
OPA Gatekeeper for Kubernetes
To leverage the power of OPA (Open Policy Agent) as an admission controller, the Kubernetes community developed Gatekeeper. Gatekeeper is a specific implementation that acts as a dynamic admission webhook for Kubernetes.
It uses OPA’s policy engine to enforce custom policies, known as Constraints. Key benefits of using Gatekeeper for Kubernetes security include:
- Declarative Policy Management: Policies are defined as Kubernetes Custom Resource Definitions (CRDs), which means they can be managed using standard Kubernetes tooling like kubectl and version-controlled via GitOps.
- Constraint Templates: Gatekeeper introduces ConstraintTemplates, which define the schema and the Rego logic for a policy. The actual Constraints then reference the template and provide specific parameters (e.g., the name of the approved image registry).
- Audit Functionality: Gatekeeper includes an audit feature that continuously checks the live state of the cluster against the defined policies, reporting any existing violations that may have slipped through or were created before the policy was enforced. This is crucial for maintaining ongoing compliance and governance automation.
Example Policy Scenario (Kubernetes Security enforced by OPA Gatekeeper):
| Policy Goal | Policy-as-Code Implementation (Rego Logic in Gatekeeper) | Enforcement Type |
|---|---|---|
| Enforce Resource Limits | Deny any deployment/pod that does not specify CPU and memory limits. | Validating |
| Require Trusted Images | Deny any image pull from a registry that is not the internal, approved private registry. | Validating |
| Restrict Root Access | Deny containers attempting to run with privileged: true or allowPrivilegeEscalation: true. | Validating |
| Auto-Labeling | Mutate the request to inject a required team: <name> label into any new Namespace created. | Mutating |
This systematic, automated enforcement mechanism is the cornerstone of modern Cloud Native security, moving control from manual, error-prone human processes to reliable, codified checks.
Governance Automation with Policy-as-Code
The scope of policy-as-code extends far beyond mere security; it is a powerful tool for holistic governance automation. In cloud-native environments, governance involves three key pillars:
- Security Compliance: Ensuring adherence to industry standards (PCI DSS, HIPAA, GDPR) and internal security baselines. PaC automatically validates that security controls like encryption, secrets management, and network segmentation are in place.
- Operational Consistency: Enforcing best practices for reliability and stability. This includes requiring resource quotas, checking for anti-affinity rules, and ensuring all services have readiness/liveness probes. For example, a policy could enforce that all deployment names follow a specific naming convention (app-environment-service).
- Cost Control: Policies can prevent developers from provisioning overly expensive or oversized cloud resources by setting guardrails on resource limits and instance types.
By codifying these rules, organizations achieve continuous compliance, a key objective of Cloud Native security. Every action in the cluster is instantly evaluated against the central policy repository, creating a real-time feedback loop.
Conclusion: The Future is Codified and Automated
Cloud Native security demands a paradigm shift, and policy-as-code is the answer. It moves security and compliance from a manual, reactive bottleneck to an automated, proactive enabler of velocity. Tools like OPA (Open Policy Agent) and its integration with admission controllers in Kubernetes security via Gatekeeper provide the technical backbone for this transformation.
By making governance automation an inherent part of the CI/CD pipeline, organizations can achieve continuous security, reduce the risk of critical misconfigurations, and scale their operations while maintaining strict compliance. Defining and enforcing security and governance policies programmatically across cloud-native environments like Kubernetes is no longer a best practice—it is a mandatory foundation for any modern, secure, and agile technology stack. The future of cloud security is one where policy is treated just like application code: versioned, tested, and automatically enforced.