Secure your data with quantum-safe encryption.
Post-Quantum Cryptography (PQC) Readiness: Navigating the Quantum Transition
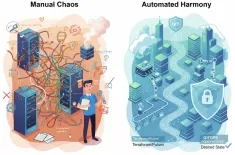
The dawn of the quantum computing era brings with it a paradox of progress. While quantum computers promise to revolutionize fields like drug discovery and material science, they simultaneously threaten the bedrock of modern digital security. This looming threat has ignited an urgent global effort to develop and deploy Post-Quantum Cryptography (PQC). As we move through 2025, the transition from classical encryption to quantum-resistant encryption has shifted from a theoretical discussion to a critical compliance and operational mandate.
The Quantum Threat: Why PQC Readiness is Non-Negotiable
Traditional public-key infrastructure (PKI) relies on mathematical problems—such as integer factorization and discrete logarithms—that are easy for classical computers to compute but virtually impossible to reverse. However, Shor’s Algorithm, a quantum algorithm, can solve these problems exponentially faster.
A sufficiently powerful, large-scale quantum computer could dismantle the security of RSA and Elliptic Curve Cryptography (ECC), which currently protect everything from banking transactions to secure messaging and government secrets. The concern isn't just about a future "Q-Day"—the day a quantum computer can break current codes—but also about "Harvest Now, Decrypt Later" (HNDL) attacks. Adversaries are currently collecting encrypted data, waiting for the technology to mature so they can decrypt it retrospectively.
The Pillars of PQC: Algorithms and Standards
To counter this, the National Institute of Standards and Technology (NIST) and other global bodies have spent years vetting new mathematical foundations that are resistant to both classical and quantum attacks.
Finalized PQC Standards
In late 2024 and early 2025, the first set of official PQC standards reached finalization. These provide the blueprints for developers to integrate security into software and hardware.
| Standard | Algorithm Name | Primary Function | Mathematical Foundation |
| FIPS 203 | ML-KEM (Kyber) | Key Establishment | Module Lattice-based |
| FIPS 204 | ML-DSA (Dilithium) | Digital Signatures | Module Lattice-based |
| FIPS 205 | SLH-DSA (SPHINCS ) | Digital Signatures | Stateless Hash-based |
| FIPS 206 | FN-DSA (Falcon) | Digital Signatures | Lattice-based (Fast) |
Key Exchange Algorithms for the Future
The shift in key exchange algorithms is perhaps the most immediate priority. Modern protocols like TLS 1.3 are already being updated to support hybrid modes. A hybrid approach combines a classical algorithm (like X25519) with a post-quantum one (like ML-KEM). This ensures that the connection remains secure even if one of the two algorithms is found to have a vulnerability, providing a "safety net" during the early years of deployment.
The Roadmap: Executing a PQC Migration
A successful PQC migration is not a simple "search and replace" of code. It is a multi-year architectural overhaul that requires high-level coordination and "crypto-agility"—the ability to swap cryptographic primitives without rebuilding entire systems.
1. Cryptographic Discovery and Inventory
You cannot protect what you do not know exists. Organizations must begin by identifying every instance of cryptography in their environment.
-
Protocols: TLS, SSH, IPsec, and VPNs.
-
Assets: Digital certificates, hardware security modules (HSMs), and code-signing keys.
-
Dependencies: Third-party libraries (OpenSSL, BouncyCastle) and vendor-supplied software.
2. Risk Assessment and Prioritization
Not all data requires immediate PQC protection. Priority should be given to:
-
Long-lived data: Information that must remain confidential for 10 years (e.g., healthcare records, national security).
-
Critical Infrastructure: Systems controlling power, finance, or communications.
-
Root of Trust: Upgrading HSMs and Root CAs that anchor the entire security chain.
3. Implementing Crypto-Agility
The goal is to move away from hardcoded encryption. By using abstraction layers and modern cryptographic providers, enterprises can ensure they are ready to update algorithms as new PQC standards evolve or if a specific algorithm is deprecated due to a newly discovered flaw.
Global Efforts and Regulatory Pressure
The move toward quantum-resistant encryption is being driven by more than just technical necessity; it is now a regulatory requirement.
-
United States: The Quantum Cybersecurity Preparedness Act and NSM-10 mandate that federal agencies inventory systems and begin the transition, with a goal of full migration for most systems by 2035.
-
Europe: ENISA and various national agencies (like BSI in Germany and ANSSI in France) have issued guidance urging the adoption of hybrid PQC schemes for critical infrastructure.
-
Industry Adoption: Tech giants like Google, Microsoft, and Cloudflare have already begun deploying ML-KEM and ML-DSA across their internal networks and public-facing services.
Challenges in the PQC Era
The transition is fraught with technical hurdles. PQC algorithms often require:
-
Larger Key Sizes: Lattice-based keys and signatures are significantly larger than RSA or ECC equivalents, which can lead to packet fragmentation in network protocols.
-
Computational Overhead: While some PQC algorithms are faster at signing, others require more memory or processing power, which can impact performance on constrained devices (IoT).
-
Compatibility Issues: Older legacy systems may not be able to handle the increased data sizes or new mathematical operations, requiring hardware replacements.
Conclusion: Starting Your Journey Today
Post-Quantum Cryptography (PQC) readiness is the defining cybersecurity challenge of the decade. While the threat of a functional quantum cracker may still be years away, the "Harvest Now, Decrypt Later" strategy makes every day of delay a risk to future privacy.
By focusing on PQC migration strategies today—starting with a comprehensive inventory and the adoption of quantum-resistant encryption in hybrid modes—organizations can ensure they remain resilient in the face of the quantum revolution. The global standard is set; the only question is how quickly your organization can adapt.