Explore how Enterprise DLT and permissioned blockchains drive supply chain transparency, decentralized identity (DID)
In the rapidly evolving landscape of 2025, the transition from centralized databases to decentralized architectures has become a strategic imperative for global organizations. Enterprise DLT (Distributed Ledger Technology) has moved beyond the experimental "Proof of Concept" phase to become a foundational pillar of modern industrial infrastructure. Unlike the volatile public blockchains associated with cryptocurrencies, enterprise-grade solutions focus on stability, compliance, and controlled access.
The Rise of Permissioned Blockchain in Industry
The primary distinction in corporate adoption is the move toward a permissioned blockchain. In this environment, the identity of every participant is known, and access to the ledger is strictly regulated. This allows major corporations to maintain the privacy of sensitive commercial data while still benefiting from the core strengths of DLT: immutability, transparency, and high availability.
For a global enterprise, a permissioned network acts as a "single source of truth." When multiple parties—such as manufacturers, logistics providers, and banks—interact on the same ledger, the need for manual reconciliation of records vanishes. Each transaction is cryptographically signed and added to a chain that cannot be altered, creating a permanent, auditable history of business activities.
Why Consortiums are Winning
Most large-scale implementations today are "Consortium Blockchains." Instead of one company owning the data, a group of industry leaders (e.g., a group of global shipping lines or a network of pharmaceutical companies) governs the network. This shared governance model ensures that no single entity can manipulate the ledger, fostering a level of trust that was previously impossible in competitive markets.
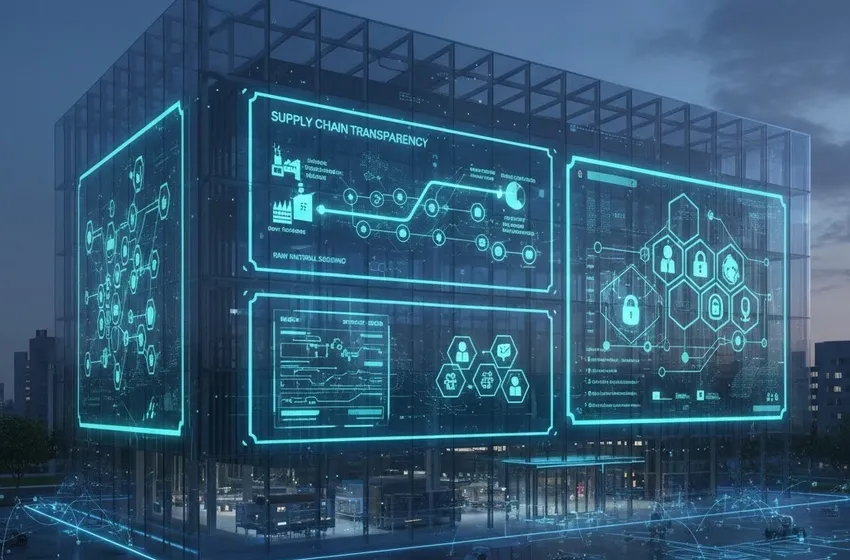
Supply Chain Transparency: From Origin to Consumer
One of the most transformative applications of DLT is achieving end-to-end supply chain transparency. Historically, supply chains have been "black boxes," where data silos between different vendors led to inefficiencies, fraud, and difficulty in tracking product provenance.
By integrating DLT, enterprises can create a "Digital Product Passport." Every step of a product’s journey is recorded:
-
Raw Material Sourcing: Verifying ethical mining or sustainable farming practices.
-
Logistics: Real-time tracking of location and environmental conditions (e.g., temperature for vaccines) via IoT integration.
-
Compliance: Instant verification of customs documentation and tax filings.
This level of transparency does more than just improve efficiency; it protects brand reputation. In the event of a product recall, a DLT-enabled system can identify the exact batch and its current location in seconds, rather than weeks, potentially saving lives and millions in costs.
Decentralized Identity (DID) and the Human Element
As enterprises digitize, managing the identities of employees, contractors, and automated devices has become a massive security risk. Traditional centralized identity systems are "honey pots" for hackers. To solve this, corporations are adopting decentralized identity (DID).
Under a DID framework:
-
Self-Sovereignty: Users (or devices) hold their own identity credentials in a secure digital wallet.
-
Verifiable Credentials: Instead of sharing a full passport scan or social security number, a user presents a "proof" that is cryptographically signed by an issuer (like a government or a previous employer).
-
Zero-Knowledge Proofs: An employee can prove they have "Level 4 Security Clearance" without the system ever seeing the underlying documents.
This approach significantly reduces the "attack surface" of an enterprise. If a central server is breached, there are no passwords or personal identity records to steal, as the data remains with the individual owners.
Secure Data Sharing and Collaboration
In the modern economy, data is a liquid asset. However, the fear of data leaks often prevents companies from collaborating on sensitive projects. Secure data sharing via DLT allows for "collaboration without exposure."
Through smart contracts—self-executing code on the ledger—enterprises can define exactly who can see what data and under what conditions. For example, two competing airlines might share maintenance data for a specific engine type to improve safety, using DLT to ensure that their proprietary passenger lists remain strictly private.
Verifiable Data Trails and Regulatory Compliance
With the introduction of strict data regulations like GDPR and various ESG (Environmental, Social, and Governance) reporting mandates, the "audit trail" has become a boardroom priority. DLT provides an automated, verifiable data trail that makes auditing a "push-button" process.
Regulators can be given "read-only" nodes on a consortium blockchain, allowing them to verify compliance in real-time. This eliminates the need for periodic, disruptive audits and ensures that reports are based on live, unalterable data rather than retrospective spreadsheets.
Strategic Implementation: Best Practices for 2025
For enterprises looking to integrate these technologies, the focus should be on interoperability and scalability.
| Feature | Description | Business Value |
| Interoperability | The ability to communicate with other DLT networks and legacy ERP systems. | Prevents "new silos" and ensures long-term viability. |
| Scalability | Support for high transaction throughput (10,000 TPS). | Necessary for global logistics and high-frequency finance. |
| Hybrid Models | Combining private data storage with public ledger anchoring. | Balances extreme privacy with public verifiability. |