Learn about secure sandboxing and WASI in 2025.
The Rise of the Universal Runtime
For decades, developers have chased the "Write Once, Run Anywhere" dream. While Docker brought us closer by packaging the entire operating system user space, it came with significant baggage: large image sizes, slow "cold start" times, and a complex security surface area.
WebAssembly (Wasm) offers a different path. It is a binary instruction format for a stack-based virtual machine, designed to be:
- Language Agnostic: Compile Rust, C , Go, Zig, or even Python into a single .wasm binary.
- Architecture Neutral: Run the same binary on x86, ARM, or RISC-V without recompilation.
- Lightweight: Wasm modules are often kilobytes in size, compared to the hundreds of megabytes required for a typical Docker container.
Why 2025 is the Year of Cloud-Native Wasm
As of Q3 2025, over 56% of backend developers are identified as "cloud-native." The industry is moving away from monolithic "heavy" containers toward cloud-native Wasm. This shift is driven by the need for extreme efficiency. In a world of high cloud costs and energy-conscious computing, running a 10MB Wasm module that starts in 10 microseconds is objectively better than running a 500MB container that takes 2 seconds to warm up.
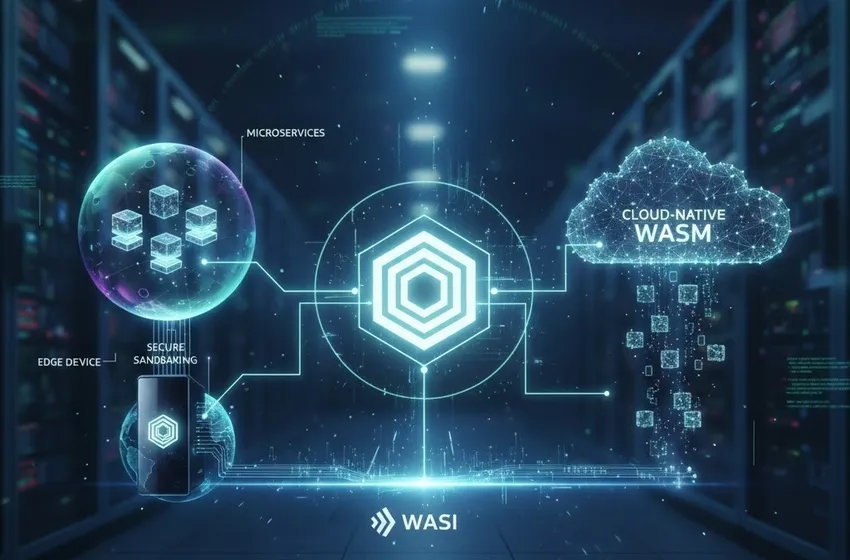
Secure Sandboxing: Security by Default
One of the most compelling reasons to move WebAssembly (Wasm) to the server is its secure sandboxing model. Unlike traditional native binaries or even some container configurations, Wasm operates in a "deny-by-default" environment.
A Wasm module has no access to the host file system, network, or hardware unless explicitly granted by the host runtime. This is known as capability-based security.
The Role of WASI (WebAssembly System Interface)
To make Wasm outside browser use cases practical, the community developed WASI. Think of WASI as the "OS for Wasm." It provides a standardized set of APIs that allow Wasm modules to interact with system resources like:
- File I/O
- Clock and timers
- Random number generation
- Network sockets (standardized in WASI Preview 2)
Because these interfaces are standardized, a Wasm module compiled for WASI can run on any compliant runtime, whether it's Wasmtime, Wasmer, or WasmEdge.
WebAssembly for Microservices and Serverless
In the world of microservices, Wasm is solving the "Cold Start" problem that has long plagued Function-as-a-Service (FaaS) providers.
Instant Scaling
When a request hits a serverless function, the provider must "spin up" the code. With traditional containers, this involves mounting a file system and starting a guest OS kernel—a process that takes hundreds of milliseconds.
Cloud-native Wasm runtimes can instantiate a module in less than a millisecond. This allows for:
- True Scale-to-Zero: You don't need to keep "warm" instances running, saving massive amounts of compute cost.
- High Density: You can run thousands of isolated Wasm microservices on a single server, whereas a similar server might only handle a few dozen Docker containers.
Sidecars and Service Meshes
Modern architectures use "sidecars" (like Envoy or Istio) to handle networking and security. By using Wasm as the plugin format for these sidecars, developers can inject custom logic (like custom headers or authentication) without restarting the entire mesh, all while maintaining high-speed execution.
Wasm at the Edge: Bringing Compute to the Data
The "Edge" refers to computing that happens physically close to the user—at a CDN node, a 5G cell tower, or an IoT gateway. This is where WebAssembly (Wasm) truly outshines every other technology.
Use Cases for Edge Wasm
- IoT and Embedded Devices: Devices with limited RAM (measured in MBs, not GBs) cannot run Docker. However, they can easily run a Wasm runtime like WAMR (WebAssembly Micro Runtime). This allows manufacturers to push over-the-air (OTA) logic updates to factory sensors or smart home devices safely.
- Content Delivery Networks (CDNs): Platforms like Cloudflare Workers and Fastly Compute@Edge use Wasm to process requests at the edge. This includes real-time image resizing, A/B testing, and AI inference—all happening within a few miles of the end-user to minimize latency.
- AI Inference: In 2025, running small "Large Language Models" (SLMs) or computer vision models at the edge is standard. Wasm provides a portable way to execute these models across various hardware accelerators (GPUs and NPUs) without needing specific drivers for every device.
Comparison: Wasm vs. Containers
| Feature | Docker Containers | WebAssembly (Wasm) |
|---|---|---|
| Isolation | OS-level (Namespaces/Cgroups) | Process-level (Software Sandbox) |
| Startup Time | 100ms - 2s | < 1ms |
| Payload Size | 100MB - 1GB | 10KB - 10MB |
| Security | Shared Kernel (Large attack surface) | Capability-based (Tiny attack surface) |
| Maturity | Very High | Growing Rapidly |
| Best For | Legacy apps, full OS needs | Microservices, Edge, Plugins |
Conclusion
The journey of WebAssembly (Wasm) from a browser optimization tool to a universal runtime is one of the most significant shifts in software engineering this decade. By providing a lightweight, secure, and portable execution environment, Wasm is enabling a new generation of cloud-native Wasm applications that are faster, safer, and cheaper to run.
Whether you are building high-performance microservices, deploying logic to edge devices, or creating a plugin system for your SaaS, Wasm offers the secure sandboxing and performance required for the modern distributed web.